3CX – Affordable Business VoIP Solution

Communication is an essential part of any business. With the rapid pace in which technology is developing at the moment, there are several different communication channels one can utilise. Nevertheless, the importance of the telephone is something which will never be overlooked and so it lies at the heart of a company’s communication.
3CX is a global leader in business VoIP and Unified Communications (UC) technology and is the preferred VoIP solutions for many businesses. It is trusted around the globe with more than 250,000 businesses, in more than 190 countries, across almost all industries. This is comes as no surprise as it offers their clients a highly affordable and easy to use system, meeting all communication standards and needs. Along with the reduced costs, 3CX is guaranteed to increase productivity and positive customer service feedback.

It is no surprise that the industry has recognised 3CX as the best option for VoIP, and therefore, has awarded numerous awards each year. If you would like to see these prestigious awards, click here.
Additionally, there are a growing number of positive case studies from almost all areas of business, including leading brand names, and even governmental institutions. If you would like to read up on these case studies, click here.
Before we go deeper into what 3CX has to offer, let’s have a look at the most commonly asked questions on VoIP in general.
What is VoIP?
Voice over Internet Protocol, or Voice over IP, is a technology which converts speech into computer data packets so it can be transmitted over computer networks and the Internet. For years Skype have been providing software that utilises VoIP technology to enable users to communicate over the internet with phones and video calls. Use of these technologies has boomed since the advent and more widely take up of broadband solutions for home and business users.
Why Switch to VoIP
There are many reasons why you should switch your traditional business phone system to a VoIP system. The pure practicality of them is a major factor in making the switch. For example, VoIP allows you to make and receive calls, even when you are away from the office. Due to VoIP being internet based, it allows you to connect to any internet device and make those important calls over you VoIP telephone network. Costs of calls are also reduced do to it being based over the internet. It can even allow you to make cost effective long distance calls.
One of the major benefits of switching to a VoIP system is that you can easily add on extensions onto the system when new employees begin with your company. This means that it can dramatically reduce costs on the additional cabling that would be needed with a traditional system.
Installing a VoIP system can completely change the way all of your business calls are handled. VoIP allows you to set up call forwarding if there is no one to take a certain call. This is especially useful in a sales environment when telephone lines are busy. The caller can be diverted to a receptionist who will take down the customer’s information and schedule one of the sales team to call back at a specific time.
Another benefit of VoIP is that it makes it easy to collaborate with other colleagues in real time. It also gives the option of video conferencing with is useful when doing demonstrations.
One of the major key benefits of implementing a VoIP system is that it allows employees to be more productive by allowing them to make and receive calls anywhere, as long as there is a data connection that will enable them to make the call. This is just the tip of the iceberg in relation to the capabilities of installing a VoIP system. There are many more features that make them a no brainer. In addition to these benefits, VoIP systems are relatively cheap and very easy to use which is why thousands of companies worldwide are benefiting from this technology.
Advantages of VoIP
The principal benefit to VoIP is price.
VoIP services have the ability to offer discounted calls, as well as many common phone features at extremely low monthly prices. It is becoming clear that traditional phone companies cannot compete.
- National – 85%
- International (Depends on destination) – Up to 80%
- Cellular – 55%
- Pure Per second billing vs Telkom charged in 30second increments
Location independence.
A 087 number is not tied to a specific area or line, you will appear to be a national company and you can keep the same number wherever you go. Because a VoIP system works primarily off of an Internet connection, the system isn’t able to distinguish how far away the recipient of the call is in relation to the caller, making each phone call standard and affordably priced. You do however have the option for other numbers such as 011, 012, 021, 031 etc – just enquire with your provider.
Using existing infrastructure
Voice traffic requires a minimum of Cat5e cabling, Layer 2 Network Hubs to maximise voice quality alongside data traffic on the same cable and preferably POE switches. One network point is shared between the Phone and the computer desktop / Notebook.
Focus on core business capabilities
By removing the worry and maintenance of phone systems, organisations can better focus on their core business capabilities. The management of these increasingly complex business communications systems is outsourced and handled offsite, so the telephony system continues to work while employees can get on with their jobs safe in the knowledge that the telephony system will just work, whenever they need it to, and they can access features like voice and video without having to know why and how they work

Now that we have a better understanding on what VoIP is, let’s get into further detail on 3CX Phone Systems.
3CX Phone System for Windows is an award-winning software-based IP PBX that replaces a proprietary hardware PABX. 3CX’s IP PBX has been developed specifically for Microsoft Windows and is based on the SIP standard, making it easier to manage and allowing you to use any SIP phone (software or hardware) from any vendor, VoIP service providers and VoIP gateways to connect traditional PSTN lines.
3CX Phone System is far less expensive than a traditional PBX and can reduce call costs substantially by using a VoIP service provider. Its web-based administration makes phone system management easy on location or remotely, making 90% of supports remotely saving on technician call out time.
3CX Phone System for Windows delivers Unified Communications technology by unifying voice mail, fax and email; as well as providing presence information.
With 3CX, employees can easily see the presence of other users and avoid unnecessarily making or transferring calls. Presence is displayed in any standards-based IP phone, as well as in the 3CX Phone user portal. Furthermore, 3CX unifies voice mail and faxes with email by delivering them to the user’s inbox.
3CX Phone System includes enterprise-level features as standard. Businesses do not need to pay extra for advanced features or add-ons, as these are incorporated in the software:
Conference Calling, Call Recording, Built-in fax server, Voice Mail, Central Phonebook, Digital receptionist (IVR), paging/ Intercom, Call Logging, Call Reporting, Call Forward on Busy or No Answer, Caller ID, Music on Hold, Follow Me / forward to Mobile and more.
Tele-work – Traditional telephony systems are highly desk bound, which in today’s world is no longer the ideal scenario. A 3CX VoIP solution gives businesses the ability to gain access to constant connectivity and productivity anywhere, anytime, whether employees are at their desks, in the boardroom or on the road. Workers can access the communication features of the VoIP system no matter where they are, improving productivity dramatically.

Porting your existing number, what does this mean?
Porting is the ability for customers to transfer their geographic telephone numbers (012, 011, 031) between Network Operators when they switch from one fixed line Network Operator to another. When you change networks but keep your number(s), you “port” your number(s) to another Network Operator.
Why would I port my number?
There are a number of reasons for porting your number to 3Gi VX network in particular:
- Increase overall savings by routing all in and outbound calls via 3Gi VX network, without publishing a new number
- Use an alternate telecoms provider other than the current network operator
- Improved service compared to current network operator
- One point of contact for voice and data requirements, no need to involve other network operators
- Detailed and informative reporting on voice
- Proactive monitoring on the voice service
- Redundancy for voice
If I port my numbers, what numbers will reflect on the recipient phone?
- By default, CLI will be activated to show the main number only or any DDI number
- If it is a requirement, CLI can be blocked to show “Private Number”

Maintenance and support
By removing the worry and maintenance of phone systems, organisations can better focus on their core business capabilities.
3CX has a build in network monitoring system that enables us to set triggers against certain critical components of the solution. The system will send E-mail alerts to key people when these triggers are hit. B&D System Engineers would require remote access to your system where 95% of support on a 3CX solution can happen within minutes remotely.

3CX Delivers Unified Communications Out of the Box
Until very recently, voice and data communications in the business environment were not unified. Telephones were simple black boxes sitting on the users’ desks, connected via their own network and completely isolated from the company’s computer data network.
With the evolution of telephony toward IP (internet protocol), the integration of both communication worlds has become possible, allowing for companies to transform their business processes. This development of breaking down communication barriers and allowing people using different forms of communication, different devices, and different media to communicate to anyone, anywhere and at any time is known as Unified Communications.
3CX Phone System for Windows is a revolutionary IP PBX that delivers unified communications technology by merging voice and data networks, allowing businesses to simplify real time delivery of information and ensure ease of use. With 3CX IP PBX, collaboration between co-workers is made easier and cooperation with business partners and clients becomes more direct, even when the parties are not located in the same place.
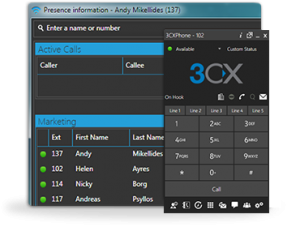
Microsoft Outlook Integration
3CX Phone System includes full Microsoft Outlook CRM integration as standard with all commercial editions of version 10. To integrate Outlook with 3CX, you will need to use 3CX Phone, which comes bundled with 3CX Phone System 10.
This article demonstrates how to integrate Outlook using 3CX Phone, how to launch calls, what in-bound call pop-ups are and how to view all calls via Outlook’s journal.
The Benefits of Integrating Microsoft Outlook with 3CX Phone System
Integrating 3CX with Outlook provides the following features:
Click-To-Call
To call a customer within Outlook, simply click on the customer contact. There’s no need to input the customer’s number into your phone, which saves you and your employees time.
Call Pop-ups
In-bound calls will pop-up on your screen, letting you know which customer is calling. This saves your company time, as your customer’s details are instantly brought up on the screen. If you do not have the customer’s details stored within Outlook, you can create a new contact record.
Call Journals
All in-bound, out-bound and missed calls are stored in the customer’s contact journal, allowing you to track the calls that were made to that customer.
For the PBX and the STD edition, you can download the 3CXPlugins. For the PRO edition you can download it within the management console.

3CX Pro Edition
The 3CX Phone System Pro edition provides professional call center features at an affordable price for any size of business. Boost your customer care agents’ productivity by reviewing real time queue and agent statistics. Supervisors can review the number of calls in a queue, how many calls have been answered or unanswered, average and longest wait-times and more.
Experience premium call Center features such as:
- Advanced Contact Center Reporting
- Advanced Queue Strategies and Real-Time Statistics
- Call Back feature, customers can hang up after a configurable length of time and maintain their position in the queue.
- Listen feature, supervisors have the ability to listen in to calls.
- The Whisper feature allows the supervisor to speak directly to an agent, giving them vital feedback whilst on the call and without the customer hearing.
- The Barge feature allows the supervisor to enter the call and assist the customer further.
- Get instantly notified when callers have been in a queue beyond the set SLA time.
- Review the time your staff logged in and out of queues.
The above features are just the tip of the ice-berg, with many more options available. With more detailed call center driven reports, you’re always up to date with how your customer care is developing.
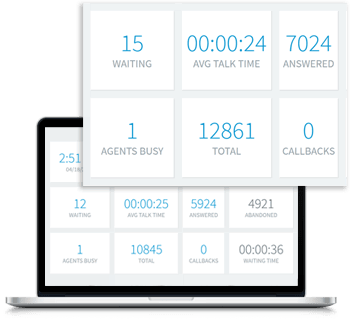
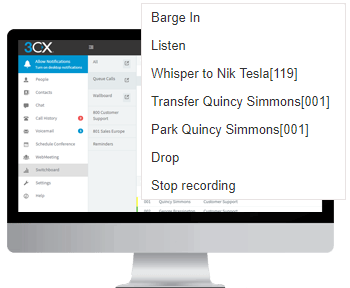
3CX Pro Integration
Integrate your favourite CRM system with ease as no plugins or manual configuration is required for any of the users. Staff can save time using click-to-call from customer records and customer call history. Management can view staff activity with detailed automatic inbound and outbound calls.

3CX Web Conferencing Made Easy
3CX’s easy to use video conferencing solution, 3CX WebMeeting, enables businesses to save time and money by hosting virtual meetings, whilst enjoying the benefits of face-to-face communication.
3CX WebMeeting can be used for a wide variety of everyday communication needs, from enriching a standard phone call with video, to visualising a sales pitch with a product presentation. Businesses can host webinars or online trainings using the Virtual Classroom features, or even provide technical support by taking control of a participant’s desktop to fix or show something on their computer.
Video conferences can easily be launched through the 3CXPhone client with a few mouse-clicks. Fully integrated with 3CX Phone System, 3CX WebMeeting is delivered as a hosted add-on, meaning that 3CX customers can easily enjoy the web conferencing feature without installing additional server hardware or requiring additional bandwidth. All 3CX customers are automatically licensed to hold video conferences with 3CX WebMeeting for a low six month or yearly cost, offering excellent value for money

3CX Hardware
To view our available SIP phone systems, please see here.
If you would like more information on 3CX or if you are ready to get your business VoIP solution, contact us on info@3gi.co.za.